Video surveillance is one of the most effective methods of protecting all kinds of enterprises, territories and even individuals. Modern technologies have stepped far forward and have given humanity a significant range of different video surveillance methods, and one of them, which will be discussed in this article, is webcam surveillance. The one that most families have at home.
The shooting quality of modern webcams, coupled with their low cost, makes this type of video surveillance the most economical of the existing ones. The truth: why buy specialized cameras with huge resolution, spend money and time on installing them, if there is such a budget option?
Surveillance through a video camera can be useful both for domestic purposes (spying on the entrance if there are suspicious guests and / or neighbors; spying on the workplace, that is, not far from the computer), or it can replace it, because with several cameras you can deploy the whole system.
Advantages
Economy and availability. Whether a person is going to use one or two cameras for domestic purposes (without the need for Full HD), or a dozen at the workplace throughout the office, it will in any case be cheaper than full-fledged cameras with their installation, since the most expensive camera with the highest resolution costs from six thousand rubles.
Practicality and reliability. A person in need of video surveillance will only need to spend money on a camera: installation in the right place can be done independently, using improvised means, and the observation itself can be carried out from your computer, being in control of the location of the video recordings on the computer’s hard drive, recording settings, and so on.
Amount of information. As already mentioned, surveillance does not necessarily require an expensive camera with excellent image quality, and it follows that the weight of the video, regardless of its duration, will be small enough to leave precious gigabytes of hard disk for other user needs.
disadvantages
It would seem, why do we need other types of video surveillance if the webcam has all the necessary properties? Because economy and quality don't always go hand in hand. Choosing surveillance through a webcam, the user takes on a number of disadvantages:
Shooting quality. Wanting to fulfill his dream and save money in addition, a person is faced with the fact that the quality of the picture is not good enough to, for example, immediately identify the identity of a suspicious person in the entrance and thereby, in which case, facilitate the work of police officers. And if there is no lighting on the floor span, then shooting night hours becomes just a waste of hard disk space and time. This minus becomes more fatal if the camera has the best resolution: in the dark it will still be difficult to see something.
Viewing angle. If you need to monitor a vast area (warehouse, recreation, an entire street, and so on), fixed webcams without the ability to independently change the angle of surveillance force the user to place another camera in the same place so as not to lose sight of anything. If we save money, then, no matter how paradoxical it may sound, it is worth buying a more expensive camera with a movable frame.
Fragility. Historically, people don't really like being filmed without their permission. If the residents of the house themselves raised funds and donated them for the installation of professional cameras, then there are no complaints. But everything changes when a single enthusiast organizes surveillance at his own expense, which can cause a very diverse range of emotions among neighbors: from hidden indignation to open hatred and bold dismantling of a kindly arranged system.
The same reaction can be evoked at the workplace in the office, but to a lesser extent, because here you can hope for the mercy and encouragement of the boss. In any case, you will have to answer.
If you think that the disadvantages outweigh the advantages, it makes sense to get acquainted with others.
DIY installation: how does it work?
 First of all, the user needs to have the following resources:
First of all, the user needs to have the following resources:
- Webcam;
- USB extension cable (it doesn’t affect the economy in any way, it costs a penny);
- Knowledge and ability to handle drivers, software;
- Computer or laptop, depending on where the camera will be connected.
If you need remote monitoring, in online mode, you need to install a separate software that provides such an opportunity.
Remote surveillance has a number of advantages:
- Saving disk space;
- You can follow the recording from absolutely any device;
- Online monitoring allows you to react to what is happening in the frame many times faster.
Software on the example of IVideon
There is a great variety of software for the implementation of online surveillance, and even the well-known Skype is among them. The auto-accept and auto-translate feature works wonders. But one of the leading programs in this area was and remains the free IVideon.

iVideon is an easy-to-learn, intuitive online surveillance program. How does it work?
After installation, the program will require you to go through the registration procedure and select the configuration;
- After registration, a list of cameras connected to the computer will appear in the list that appears.
- The next window will give the user the opportunity to independently select the range of disk space under which the record will be allocated. Depending on the goals, cameras and their number, you need to set the desired size in gigabytes, but it is recommended to allocate at least 50-70GB for comfortable round-the-clock recording.
- Further settings will give the user the ability to automatically launch the program when the computer is turned on, start recording according to a schedule, sound, motion, and many other nice features.
The IVideon Client and IVideon Server installed also allow the user to conduct online surveillance of several cameras at once, configure access and privacy for viewing.
Other programs
In addition to the already announced programs, there are the following competitors:
WebcamXP. A shareware utility that in its free version gives users a limited range of options. In particular, there is only one tracking thread. The paid version allows you to set up motion monitoring, online broadcasting directly to the developer's website with cloud storage.
Xeota. This program allows in its trial version to monitor from four cameras simultaneously. Supports analog, web, IP and wireless cameras from the most popular publishers. In addition to covert surveillance functions, it can also be used as an alarm (with a choice of siren sound) with automatic sending of images of what is happening in the frame to a postal address or telephone.
abelcam. An online translator of images from a webcam and a video editor in one bottle. Like WebcamXP, in the trial version it allows you to monitor only one stream, one camera. Supports high-resolution cameras and the above types, .AVI and .WMV formats, has a built-in motion detector.
Globoss. A serious program that has a full range of functions: 12 cameras in the paid version (2 in the free version), noise and motion sensor, time recording, support for IP cameras, and the developer's service allows remote monitoring.
webcammonitor. A single-threaded program that supports only webcams, but has all of the above functions: a motion sensor (with the possibility of setting motion detection in only one specific area of the frame), noise (with volume control) and the ability to send warning messages to mail and phone.
AxxonNext. An impressive program that allows you to deploy a surveillance system up to sixteen cameras bypasses all the previous ones in such two functions as surveillance and full control from the phone and searching for the necessary object on the frame according to certain parameters, but is inferior in terms of convenience and attractiveness of the interface.
Home Video Streamer. Unlike all other programs, it is a multiplatform program, i.e. it has equal opportunities and the same functionality both on Windows and Ubuntu with MacOS, Android and IOS. It has a separate cloud storage and easy connection to other storages of this type. In the rest - all the same ability to record by motion, sound, time and send alarm alerts to the phone.
Eyeline Video Surveillance. The record holder for streaming support - no more, no less - one hundred cameras. A pleasant minimalistic interface and a two-week trial period with the possibility of subscribing at a symbolic price provide a full-fledged and motley functionality (Editor's choice!).
Fraps. Despite the popularity of this program as a software for capturing images from a computer screen, recent updates have introduced an innovation in the face of recording a picture from a video camera in parallel with image capture, on which you can, of course, speculate and get another video surveillance program, but very limited in functionality - no Motion sensors, sound, time recording, cloud storage and remote tracking are not available for this utility.
Useful video
See how to install home video surveillance based on a webcam with IVideon software.
Conclusion
Despite the fairly rich list of the listed online surveillance programs, not all may be suitable for a specific user, but that does not matter, because there are still many different programs on the Internet for different needs, including completely free ones.
What has not yet been said is that the availability of this type of video surveillance allows surveillance. A webcam thrown into a conference room, locker room or bag, or a laptop completely left on the table with the monitor turned off, but the camera working, can become the main trump card of attackers who want to get the necessary information for their own selfish purposes (insider information of a competitive company, blackmail of an individual) .
Be vigilant for suspiciously ownerless equipment in the workplace and for your personal belongings. We hope that this article will serve those in need for peaceful purposes.
Greetings dear reader! Since you are on this page of my site, then most likely you are interested in: how to make a surveillance camera out of a webcam or, Is it possible to use a regular webcam as video surveillance?
iSpy is a free computer program that is a powerful system for video surveillance. It is intended to ensure the safety of the premises, and notify their owners in the event of unauthorized entry into the house. The application is capable of using webcams and microphones to recognize and record any movements or sounds in the monitored room. Also, the program provides recording only on alarm, that is: Shooting will start only at the moment of the appearance of movement in the range of visibility of the camera, or when sound vibrations appear. In general, to put it simply, the program can work as a motion sensor. 
The iSpy application allows its users to not only watch online everything that happens in the webcam's field of view, but also record video at the same time and view it later. The video itself is saved in the selected format, which can be played on any media player, as well as in a regular web browser. The recorded video can be saved not only on your computer, but also on remote servers of the company that developed the iSpy application.
iSpy has the ability (from anywhere) to receive and transmit received data from one computer to another, provided that they are connected to a single system and have Internet access. This system is somewhat reminiscent of cloud technology - virtual file storage. This thing is very convenient if you want to avoid data storage problems and ensure their complete security.
The application also has the function of sending SMS messages to the phone or letters to EMail: after a certain amount of time (with attached images), or in case of detecting any movements or sounds. This is very convenient, especially when you are away on a business trip or vacation.
One of the main advantages of the iSpy application is the ability to monitor from an unlimited number of computers that can be combined into one network.
Advantages of the iSpy program:
covert surveillance through a laptop or computer webcam;
detection and recording of any movement;
Recognizes not only movements, but also sounds;
Can work with an unlimited number of surveillance equipment;
Possibility of combining several computers into one system;
sending notifications to the phone or e-mail (with attached photos);
Possibility to work remotely;
· has a good security system, with the help of various passwords;
The application can be downloaded completely free of charge on the developer's website or via a direct link from Yandex disk (). On the manufacturer's website, the program does not have the Russian language. I have a multilingual version of the program on Yandex disk, including Russian.
After installing and running the program, to install the Russian language, go to the "Options" tab
The next step is to select the type of video camera to be connected:
Protecting your apartment from strangers is easy enough, and iSpy is a worthy option for solving this problem!
As you know, even if you are paranoid, it does not mean that you are not being followed.
Today, when you absolutely right watch, this phrase is especially relevant - large companies have been monitoring your actions on the network for a long time, cyber scammers are getting accustomed to a bank account, and neural networks have learned to successfully recognize faces and find your VKontakte profile from a photo.
To maintain privacy at least at home, we recommend ours from hacking. Today we will give a number of additional recommendations for those whom the attackers were still able to hack and gain access to the PC or laptop camera.
Imagine that the camera indicator light turns on for a second and then goes out. This can be a wake-up call that should not be ignored (unless you want your private life to suddenly become public). But even if the indicator is off, the webcam can still work secretly.
Finding out which programs are using the camera is pretty easy.
1. First of all, you will need special software that will show all the processes associated with a particular device. For this purpose, we suggest using Process Explorer. This handy program is available online and offline.
2. Then you need to find out the name of the webcam in the system (in Russian versions of Windows, it sounds like "Physical Device Object Name"). It is not difficult to find this information: Start - Control Panel - Hardware and Sound - Device Manager.
3. Next, "Image Processing Devices" - "Properties" of the camera - the "Details" tab. In the drop-down list, select "Physical Device Object Name", which looks something like this: "\Device\0000009c". Right click on it and click "Copy".
4. Now we go to Process Explorer, open the search by the button with the binoculars icon (or the combination Ctrl + F), insert the "Physical Device Object Name" and start the search to find all the processes using your webcam.
If no suspicious activity is detected, there is nothing to worry about. Usually, you will only find Skype or other video calling apps on this list. However, do not be too lazy to check the launch path. Attackers often try to pass off a malicious program as a legitimate application, taking advantage of the inattention of ordinary users.
If you see suspicious non-system programs in the Process Explorer list that you definitely did not install, we recommend that you close this process and run the full .
P.S. The method described above can also be applied to microphones, which can also become a target for spyware.
How to check if the camera is following the user or not?
Hello, today we will talk about how to check if the webcam of your laptop or computer is working now, and the camera is now monitoring your movements, or can you pick your nose?
The fact that any mobile device is now equipped with a camera is damn convenient. Have you ever thought that the camera can shoot without your permission? After all, with its only existence it is aimed at the one who settled down in front of the monitor. That is you.
We follow further. If the camera is built-in, then the LED blinking next to it often “gives out” the work process. The same "eye" is located on the device mounted on the monitor of a stationary PC. Well… well, if so, and you suddenly noticed it. And if not, and the camera is following you right now? She can do it without blinking...
Immediately about the unpleasant.
There are a lot of options when a hacker can turn on the camera from a distance. This is usually done using two options:
- a Trojan program, and it will be compiled not only in order to broadcast the image from the camera. After all, the picture itself does not matter. Sometimes turning on the camera and subsequent recording goes along with another, huge number of programs that allow, among other things, to disable most of the Windows security features. A typical and most elementary example of such a Trojan is .
- who does not know (he meter), I advise you to get to know him at least superficially. And if in the first paragraph the dexterity of a hacker can come to naught thanks to a good anti-virus package, then there is no panacea for this - the anti-virus does not isolate an open meter session. And among the running services, recording screenshots from the screen or webcam can also be started there. Read the article at the link.
Is the camera watching? Quick option.
Let's check...
But first, I will ask you to download a very good program called Process Explorer. It is very useful for those who are interested in the nature of certain processes that take place in Windows, allowing you to track programs and programs running on the system. With its help, it is easy to detect viruses and other rubbish, which successfully disguises itself as popular processes. Program Process Explorer will appear in my articles more than once, it is high time for you to acquire it. It is in English, does not require installation, a simple executable file.
But let's get back to “our sheep” and check who the camera is following.
Download the Process Explorer program from the Microsoft website in a zip archive
To check the details of your device (yes, any!), you will need its full name. The device manager in Windows will issue it with giblets. A computer(across Start) - right mouse Properties – Device Manager.
Now find the imaging devices. Expand the item. And right click Properties. Copy the device name in the tab Device description:
Now we launch Process Explorer. It reminds me of the windows task manager. On the left in the toolbar, find the icon with binoculars. Click on it and paste what you copied. Click Search


If something has already alerted you, kill the process using the two buttons above, starting with Kill . See what happens to the performance of the camera and the program for working with the camera. If nothing happened - an option to think about the fact that someone else knows what your face looks like in front of the monitor. And the fact that the camera is watching you, consider it a proven fact.
- in order to correctly identify your camera among other devices of a computer and laptop, you will need its full name in the list of equipment. No one can tell you better than the Windows Manager. We press WIN + R, we collect a team

Copy the name from the tab Intelligence under paragraph Device description and type it in the open search box Process Explorer(CTRL+F). How to proceed, you know. Check and make sure.
How to prevent?
I'll tell you a secret - a well-hidden Trojan will hide the "process" so that no one will notice it. Therefore, make sure that the infection does not get into the computer. If there is no good antivirus package, your computer is open for surveillance. And it will solve most problems. Bypass antivirus protection, and sometimes even at the level Difender-but from Windows 10, maybe not every “hacker”. There are few professionals who will encroach on your camera. And without an antivirus, there is nothing to do on the network at all. The problem is sometimes that hackers often have very specific titles and positions.
There is an option to turn it off. And turn it on only for the duration of the session. Is the camera built in? In sure there is an option to disable the camera from there. Dance from the word camera in the CMOS settings. Use this. If you use it often, the next option is suitable.
Articles about the need to seal the front camera to protect against surveillance have been published for 15 years. I am sure that you have seen dozens of such texts. Perhaps they are sponsored by manufacturers of black electrical tape.
In 2016, a survey by Kaspersky Lab showed that 23% Russians are led to such articles and seal the camera on a laptop. Most likely, these people do not only do this, but also take other security measures. For example, they try not to leave the house. After all, seeing a computer with a sealed camera in a public place is a rare success.
But such people still exist. Their entourage is perplexed: “Are you an idiot? Who needs to look at your drunk mug? Alas, but some may still need it.
To whom?
If you work at a company computer, then you may be monitored by IT department employees or superiors. But it’s not worth defending yourself from such surveillance, otherwise they may think of you: “Is he hiding something? We should take a look at him."
Snowden and his associates promote the theory that popular operating systems take photos of the user from time to time and transfer them to their servers. But it is part of a global surveillance system that is hard to hide from. If you are a simple decent person, then you do not need to defend yourself from it.
But there are people who purposefully install surveillance software and benefit from it. Let's talk about them.
RAT-ers




All photos from the gallery above are taken from an old thread ☆ ShowCase ☆ Girl Slaves On Your RAT at hackforums.net. The hooligans hacked into the cameras of these women, took photos and posted them to show off their achievements to their comrades. Most likely, the victims will never know about it.
RAT (Remote Administration Tools or Remote Access Trojan) is software for hidden from the user remote computer control. The first such program appeared in 1998 and was called BackOrifice.
The term RAT-er was coined by BBC journalists for several years. So in the media it is customary to call hooligans who install RAT on the computers of “victims” and collect “compromising evidence” on them. More often they do it just for fun, but some make money on it.
What is RAT capable of?


In the gallery above are screenshots of the DarkComet RAT program. This is a terry classic of the genre, the most famous tool for covert control of someone else's computer, appeared back in 2008. His name sometimes even gets into the news. Rumor has it that DarkComet was used by the Syrian authorities to spy on the opposition.
The table on the left side of the screen is a list of users whose computers can be managed. On the right is a list of available actions for each. As you can see, computers are completely in the hands of scammers. You can even upload files and run bat scripts. Sections deserve special attention. Spy Functions And Fun Functions.
"Spy functions" allow you to monitor the "slave": record sound and video, do something on the desktop (something like TeamViewer), record all keystrokes. And "fun features" can scare the victim: turn off the mouse / keyboard, slide out the drive, send messages in the form of dialog boxes or chat on the computer screen. I'll clarify just in case: when RAT is running, on Windows the light near the camera in most cases does not light up.
Is it dangerous for Mac?
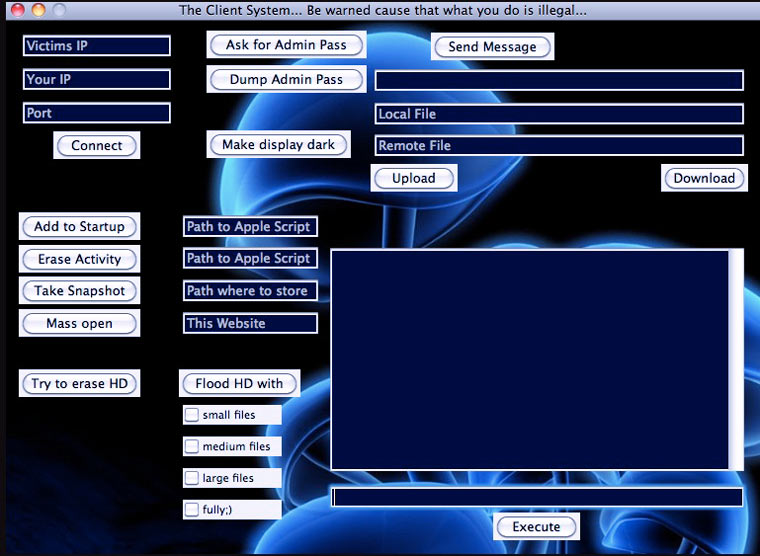
Yes. There are some flavors of RAT that work under MacOS. For example, the cross-platform Blackhole, which is shown in the picture above. It has fewer standard functions, but you can run Apple Script and Shell script scripts.
In RAT for Mac, developers often don't include features for recording video, because in OS X and MacOS they can't fight turning on the light that allows the user to detect the program's operation. Even the completely new RAT, which appeared at the end of 2016, Backdoor.OSX.Mokes.a there are only functions for recording video from the screen and sound. He does not have access to the webcam.
Is it dangerous for smartphones?

Yes, for Android. For example, the very often mentioned DroidJack. After installing this program on the victim's smartphone, the attacker gets access to her camera, microphone, contacts, SMS, calls, location, installed applications. It does not require root rights to run.
How does the RAT get on the victim's computer?

First, the RAT-er creates a file with the exe extension, the so-called "stub", in which it prescribes the necessary settings. After that, he needs to make the victim run it on his computer.
The first way is to disguise the file as something useful and convince the person to open it. For example, to the Syrian opposition mentioned above, spies sent DarkComet under the guise of a "message encryptor for Skype" and convinced them to install it to protect themselves from government surveillance.
RAT-programs are distributed as individually: “a guy gives a GDZ classmate in chemistry in the form of an exe-file” or in bulk: uploading to torrents or file exchangers under the guise of useful programs, spam in social networks, mail, forums. BlackHole, for example, was distributed under the guise of an antivirus for Mac.
The second way is to stupidly attach yourself to someone else's computer with a flash drive while its owner has left. The victims of RAT-ers are often their loved ones. In the Tor network, you can stumble upon sites with an inviting inscription on the main “Live broadcast from the front camera of my 13 year old Josie's sisters. Pay 0.01BTC ($10) and watch her 24/7.”
Appliance store clerks can install spying software on customers' computers.
Is it hard to get RAT?



The remote access program itself is easy to download. It can be found in the public domain or bought at any Tor digital goods store. Visually, a quarter of the malware that is presented there are various types of RAT.
One by one (set: proven program + very detailed instructions) they are sold at prices ranging from $0.5 to $2 dollars. Or you can buy 20-30 varieties of RAT at once in the form of a Hacker Starter Pack for $10-$50, which will include a bunch of other programs, their distribution tools, anti-virus masking (encryption) and educational literature. Documented RAT source codes can cost several hundred dollars.
The DarkComet mentioned above is a thing of the past, because the developers closed the project back in 2012. But he has hundreds analogues and clones. According to a study by the DarkReading portal, the TOP 3 RATs at the end of 2015 are Sakula, KjW0rm and Havex. But DarkComet is still in fifth place in the ranking.
How do RATs make money off girls?

The victims of RAT'ers in most cases are girls 10-18 years old. After all, it is most interesting to watch such a victim. Girls often combine taking a bath with watching a movie on a laptop, changing clothes several times a day, walking around the house half-naked, discussing the details of their intimate life with their friends.
In 2013, journalists from BBC News wrote that access to a woman's computer costs $1-$2, and men only a couple of cents. But you can’t raise a lot of money selling accesses, because looking at the camera for strangers quickly gets boring. But you can make money on erotic videos.
It is no coincidence that there are "fun features" in the RAT. They help to psychologically put pressure on the victim and force them to do something that can excite pedophile viewers. The picture above shows the horrified and helpless face of a young girl who is blackmailed through a webcam and forced to undress.
Such videos are very necessary for sites for pedophiles and sadists. On the dark web, "adult" resources with really "special" videos charge several hundred dollars. per subscription per visitor and they have the ability to pay content providers well.
How do RATs make money off boys?

Often the target of RAT-ers are the owners of upgraded accounts in popular online games. A typical story from the forums:
I went to have tea. When he returned, he saw that COMP SAM was dragging game items and exchanging them with someone.
Sometimes the owners of visited sites, blogs and pages on social networks are hacked in this way.
How to understand that the computer is infected?

Bullies don't want you to know that someone else is using your computer. Many victims of RAT-ers do not realize their fate. The analysis of the forums revealed signs that may indicate that you have become a "slave":
- The dates the files were last opened do not match the times you opened them. If you have a text file with passwords on your desktop, then pay attention to it first of all;
- When you move away from the computer, then after you find the cursor is not in the place where you left it;
- Windows and tabs in the browser suddenly open / close;
- Spam suddenly began to be sent from several of your accounts in instant messengers and social networks;
- You missed the money on your e-wallet.
What to do?

The camera should be sealed last. To avoid such a problem, you should follow the well-known security rules: do not download any garbage from left-handed sources, do not open suspicious files from mail, do not succumb to persuasion "put a program for cheating VK likes", do not let anyone work on your personal computer.